2021-08-01-Initiate-SMS-Verification-Attack¶
Incident 1 -> initiate SMS attack¶
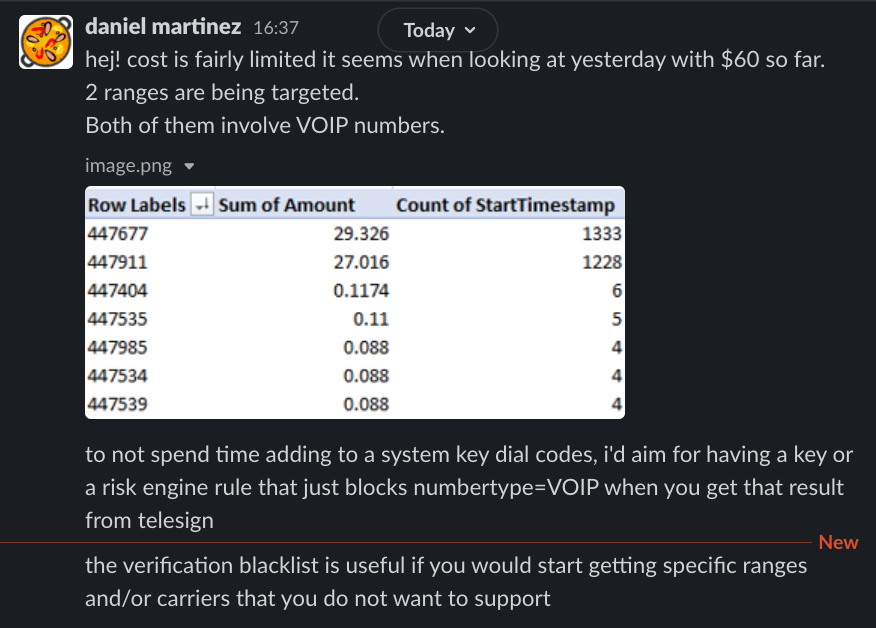
This weenend (01-Aug-21), we were attacked by high numbers of request for initiate SMSes. This increased the CPU level on VMs and also probabaly results in large SMS bills. We have a block at sinch which blocks too many SMS for a number in quick succession. But the attackers initiate very high number of request so they get high success rate. All the attacks were carried out from about 10 different IPs mostly from UK phone number ranges.
Resolution :-¶
We have rate limited the call to this api endpoint on nginx controller. This does not helps us completly blocking the attack since we use 5 pods off nginx in prod, and this rate limit is applied to each pod, attackers will still be able to make a good amount of requests. But this fix shoud limit the attack to atleast some degree.
Permanant fix - Thani is investigatng on other fixes like:-¶
1) Block the IPs of attackers
2) Block phone number ranges
3) Integrate with tele-sign to get details on phone numbers and block then if they are IP telephones.
Additional info from Dani.